<< Click here to See the list of other Ransomware Viruses & Hacker’s
Ransomware Virus GrandCrab Ransomware
THIS HACKER WAS PAID ON ON JUNE 2018 AND PROMPTLY PROVIDED THE DECRYPTION UTILITY, INSTRUCTIONS, KEY, AND SUPPORT TO DECRYPT THE FILES BACK TO NORMAL. THUS HE IS CONSIDERED HONORABLE.
| Incident Date | Ransomware Virus Strain / Name / Details | Hacker Contact / Alias / URL | Status After Payment | |
|---|---|---|---|---|
| June 2018 | GrandCrab Ransomware | http://gdcbmuveqjsli57x.onion/ |  |
Learn More |
Background:
On June 1st, 2018 it was reported to Planet Cyber, that a client is not able to open the files in any of the folders on the computer. Along with the issue, the client reported seeing a new file in all the directories of the computer “CRAB-DECRYPT.txt” which appeared to be from an unknown origin.
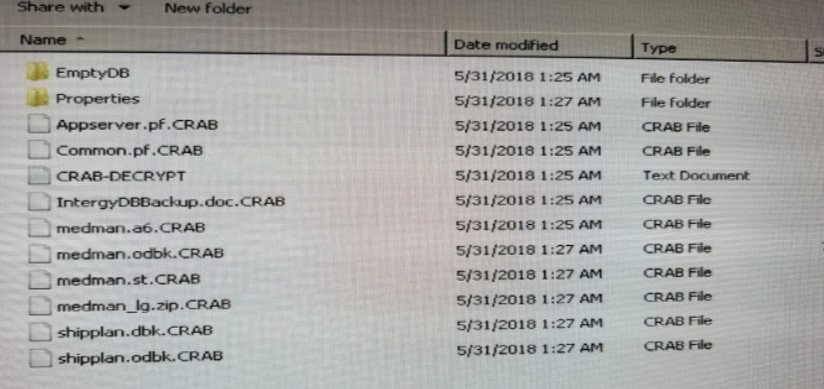
Per our instructions, the client opened and read the file, which contained a message about how the files have been encrypted and demanded the ransom money, along with the hackers communications instructions. Immediately, we instructed our client to turn off all the computers in the organization.
Planet Cyber, dispatched a senior tech to the client’s location, to assess the damage and provide ransomware incident response services.
Upon inspecting the folders on the infected machine, we confirmed the machine was hit by a new strain of ransomware virus, which encrypts the files on a machine, and added the file extension of .CRAB to all the encrypted files. After much research, and various recovery techniques we could not locate any immediate methods to reverse or unencrypt the files & documents.
We contacted the hacker, via his chat room and URL, and he promptly responded, and asked for the Ransome money 1 Bitcoin, in exchange for the decryption tool. This hacker’s website and presentation was very elaborate, automated, and well thought out. Upon visiting the URL, you could see an animated countdown, before the ransom would double, as well as a chat box, and an automated process to upload one file, to confirm he can, in fact, reverse the encryption.
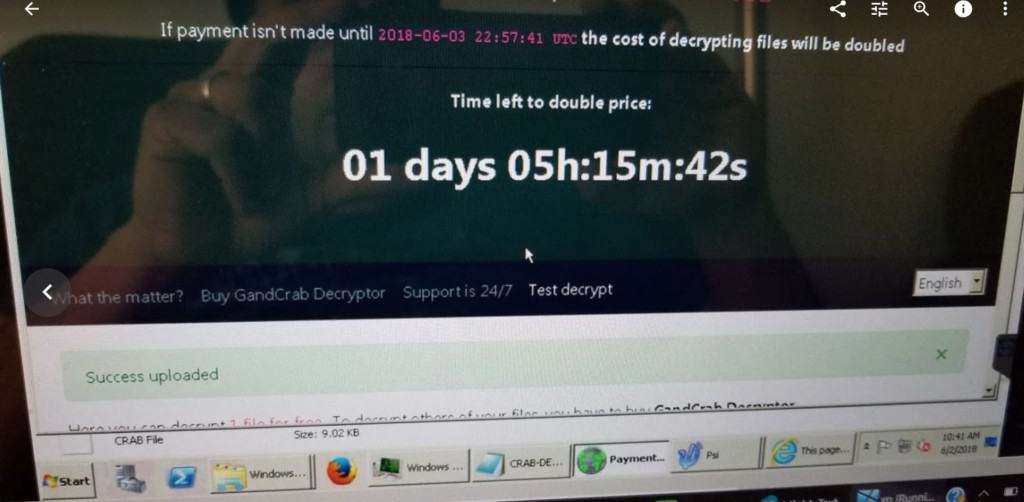
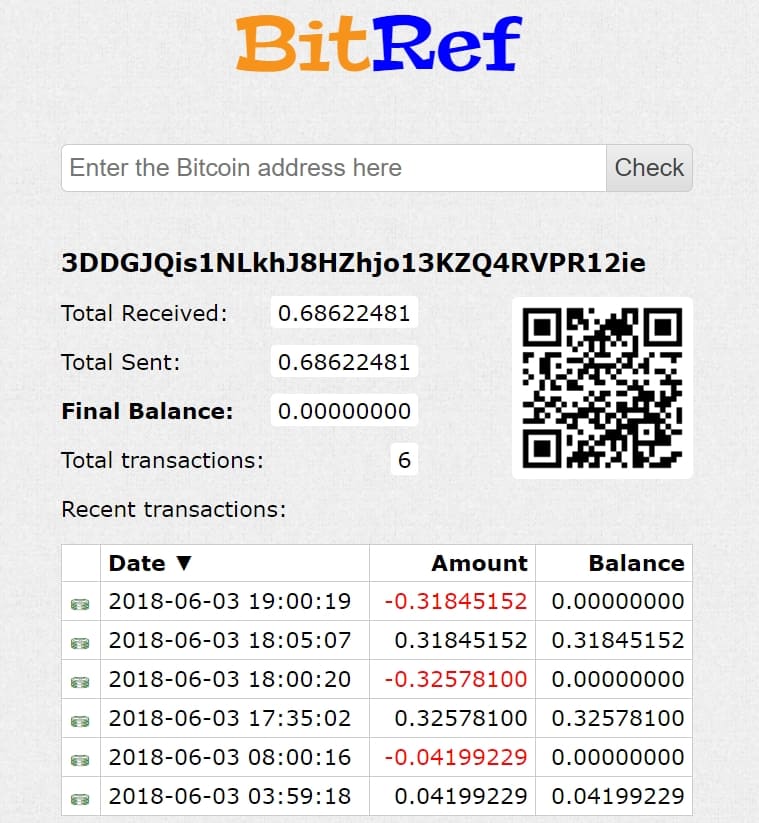
see the URL below
https://bitref.com/3DDGJQis1NLkhJ8HZhjo13KZQ4RVPR12ie
We sent the funds on 6-3-2018 and he withdrew the funds the same day.
After he received the funds, he quickly sent us the link to download the decryption utility and key, and in a matter of hours, everything was back to normal.
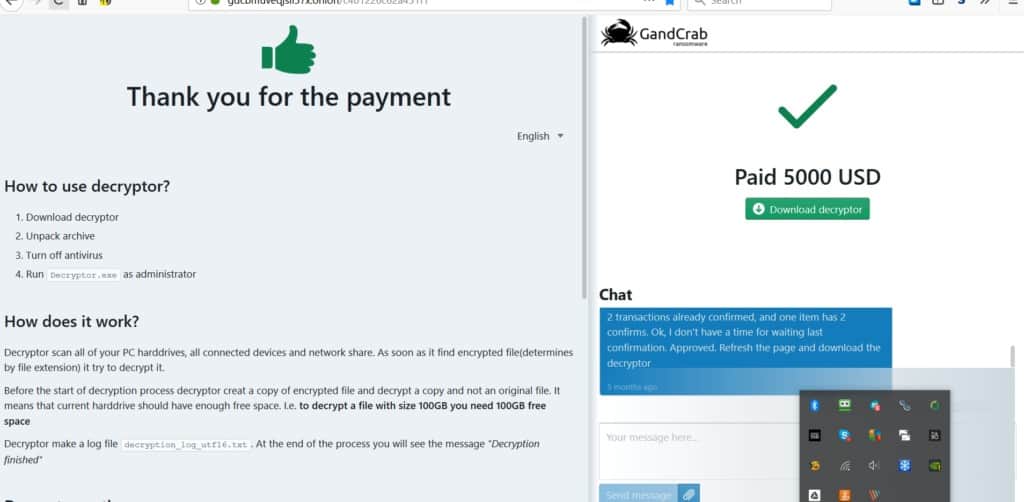
Ransomware Demand Letter:
File Name “CRAB-DECRYPT.txt”
======================================
—= GANDCRAB V3 =—
Attention!
All your files documents, photos, databases, and other important files are encrypted and have the extension “.CRAB”
The only method of recovering files is to purchase a private key. It is on our server and only we can recover your files.
The server with your key is in a closed network TOR. You can get there by the following ways:
0. Download Tor browser – https://www.torproject.org/
1. Install Tor browser
2. Open Tor Browser
3. Open link in TOR browser: http://gandcrab2pie73et.onion/[id]
4. Follow the instructions on this page
On our page you will see instructions on payment and get the opportunity to decrypt 1 file for free.
The alternative way to contact us is to use Jabber messanger. Read how to:
0. Download Psi-Plus Jabber Client: https://psi-im.org/download/
1. Register new account: http://sj.ms/register.php
0) Enter “username”: [id]
1) Enter “password”: your password
2. Add new account in Psi
3. Add and write Jabber ID: ransomware@sj.ms any message
4. Follow instruction bot
ATTENTION!
It is a bot! It’s fully automated artificial system without human control!
To contact us use TOR links. We can provide you all required proofs of decryption availibility anytime. We are open to conversations.
You can read instructions how to install and use jabber here http://www.sfu.ca/jabber/Psi_Jabber_PC.pdf
CAUGHTION!
Do not try to modify files or use your own private key. This will result in the loss of your data forever!
======================================
Background
Latest IT / Cyber Security / Cyber Attack News 11/4/2018
Ransomware Viruses are on the rise, clients have been reporting more incidents in 2018 than in any previous years. It is now super critical for all clients to (1) double check on their backups and validate them. (2) ensure you have several types of backups, such as cloud, and local external drive backups. (3) ensure your devices have adequate antivirus protection (4) and practice safe internet usage protocols, which means do not open attachments from anyone (including the people you know), try not to browse to websites which are unknown and random.
In the past several months two clients, have reported that all of their files, work documents and work applications, which maintain all their work client lists, client details, patient details, account payables etc, have all become useless and inaccessible, after realizing that their computers have become compromised, hacked, and hit with ransomware virus’s that have encrypted all of their files, with Ransome demand letters from the hackers.
Unfortunately for various reasons, our clients did not have backups, and or their backups were compromised as well, thus left with the only choice to pay the Ransome demands, which are usually in the range of 1 Bitcoin, approximately $5000 to $6500 per bitcoin. In both cases, both clients paid the Ransome demand amounts, and in one incident the hacker was honorable at the end and provided the decryption program which restores all the files back to normal working condition. And on the second incident, the hacker was not honorable and did not provide the decryption reversal tool.
Thus, for these reasons, at Planet Cyber IT Services we decided to start a new section on our website, to expose, inform, and educate the public on various ransomware incidents, and to most importantly also let the public know, of hackers whom are honorable, and hackers whom are dishonored since they did not provide the reversal decryption tool, after being paid.
We look forward to growing this list and to exposing both honorable and dishonorable hackers. We welcome other clients, victims, and cybersecurity experts to email us their incidents details so that we can add more to this list. To report new incidents, or if you have any questions please emails us at info@planetcyber.net.
